Adobe Patches One Zero Day in Flash
Adobe Patches One Zero Day in Flash and except another patch by next week.
Fiddler showing the execution of the attack
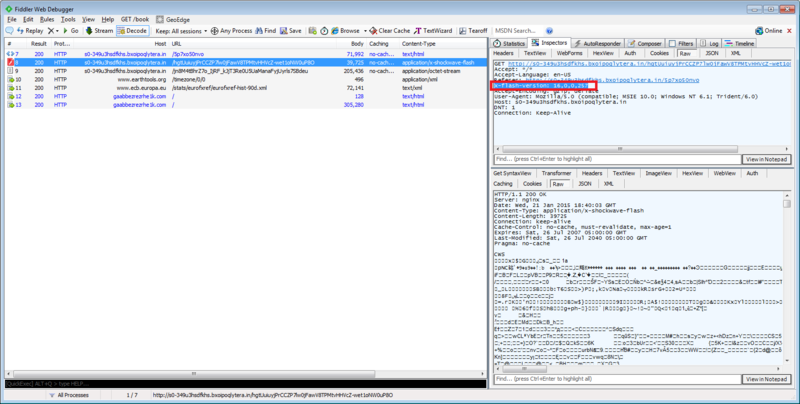
1. The user’s browser accesses the Angler exploit kit’s landing page hosted at http://s0-349u3hsdfkhs.bxoipoqlytera.in (#7). This host was specifically set up to serve this exploit kit.
2. Angler delivers the Flash zero-day (#8). Notice that the browser’s Flash plugin is patched and runs the latest version (16.0.0.257).
3. The zero day successfully infects the machine (#9).
Thanks to Kafeine for sharing this discovery with the security industry.
The vulnerability that Adobe patched Thursday is under active attack, but Adobe officials said that this flaw is not the one that security researcher Kafeine said Wednesday was being used in the Angler attacks
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh and Linux. These updates address a vulnerability that could be used to circumvent memory randomization mitigations on the Windows platform,” Adobe said in its advisory.
“Adobe is aware of reports that an exploit for CVE-2015-0310 exists in the wild, which is being used in attacks against older versions of Flash Player. Additionally, we are investigating reports that a separate exploit for Flash Player 16.0.0.287 and earlier also exists in the wild.”
“A critical vulnerability (CVE-2015-0311) exists in Adobe Flash Player 16.0.0.287 and earlier versions for Windows and Macintosh. Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system,” Adobe said in an advisory.
“We are aware of reports that this vulnerability is being actively exploited in the wild via drive-by-download attacks against systems running Internet Explorer and Firefox on Windows 8 and below.”





