End to End Encryption Isn’t So Secure After All
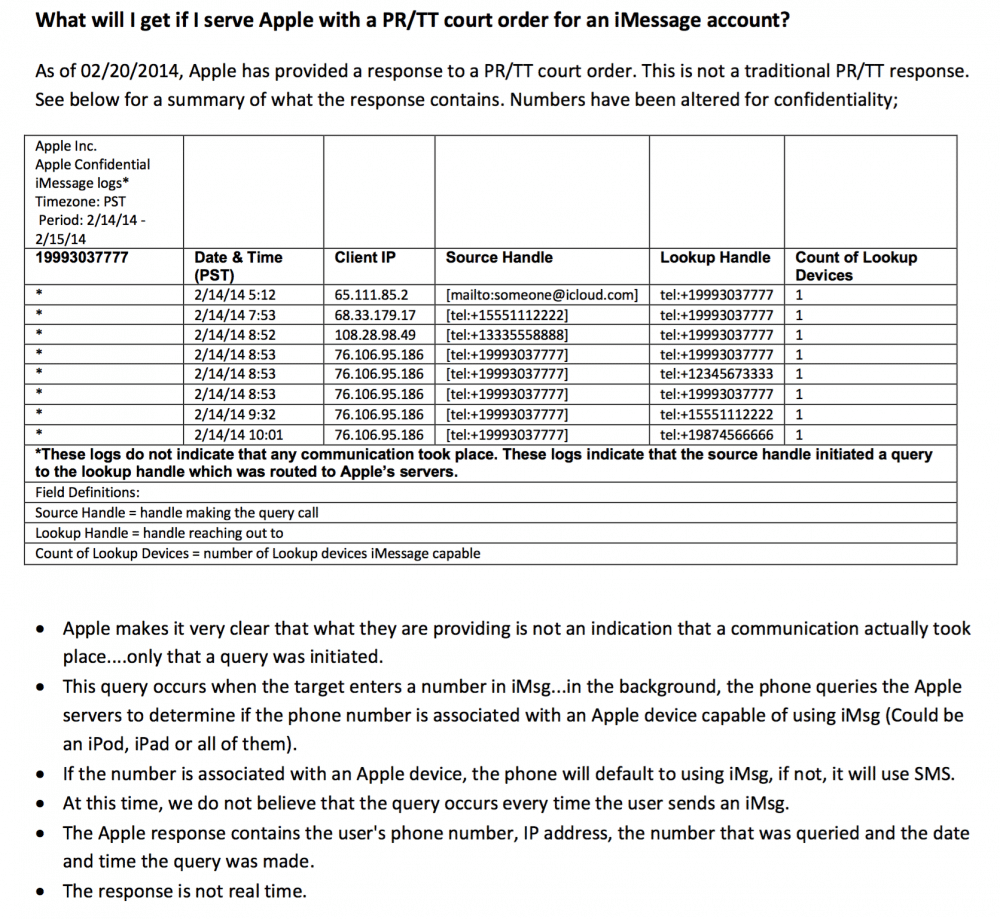
When company chooses to log information which isn’t necessary and breach privacy acts, end to end encryption is no use. Apple promises that your iMessage’s are secure and safe. Unfortunately this is not the case. Documents obtained by The Intercept, show’s that Apple logs your IP addresses and contacts stored on your phone even though no communication were carried out. Apple assures that data logging does not necessary mean communications were occurred, it is “only that a query is initiated”.
Do Apple really needs to log these information’s? How often these queries are logged and how long? The company has previously said that your iMessages and FaceTime calls are your business, not ours. … Unlike other companies’ messaging services, Apple doesn’t scan your communications, and we wouldn’t be able to comply with a wiretap order even if we wanted to.” also “For example, conversations which take place over iMessage and FaceTime are protected by end-to-end encryption so no one but the sender and receiver can see or read them. Apple cannot decrypt that data. Similarly, we do not store data related to customers’ location, Map searches or Siri requests in any identifiable form.”
Apple Towards Privacy
At Apple, your trust means everything to us. That’s why we respect your privacy and protect it with strong encryption, plus strict policies that govern how all data is handled.
Security and privacy are fundamental to the design of all our hardware, software and services, including iCloud and new services like Apple Pay. And we continue to make improvements. Two-step verification, which we encourage all our customers to use, in addition to protecting your Apple ID account information, now also protects all of the data you store and keep up to date with iCloud.