Unboxing Linux/Mumblehard: Muttering spam from your servers
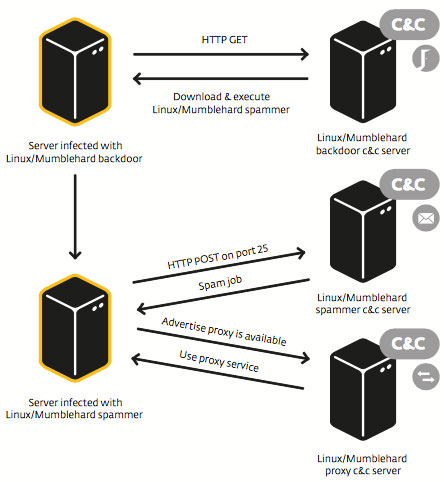
Linux/Mumblehard is a family of malware targeting servers running both the Linux and BSD operating systems. A umblehard infected server opens a backdoor for the cybercriminals that allows them full control of the system by running arbitrary code. It also has a general purpose-proxy and a module for sending spam messages.
Here are the key findings of our analysis:
• Perl scripts were packed inside ELF binaries written in assembly language, showing a higher level of sophistication than average.
• A total of 8,867 unique IP addresseswere seen in our sinkhole over a 7-month period.
• The highest number of unique IP addresses seen in a single day is as high as 3,292.
• Mumblehard has been active since at least 2009.
• Among the compromised machines, web serversare the most susceptible to being infected.
• There is a strong link between Mumblehard and Yellsoft, an online company selling software to send bulk e-mail messages.
Researchers found a malware on a server which was previously blacklisted for sending spam. They were also successful by taking control of one of the domain because the registration was expired. From there they were able to monitor and track the malware activity.
Mumblehard components are mainly Perl scripts encrypted and packed inside ELF binaries. In some cases, the Perl script contains another ELF executable with the same packer in the fashion of a Russian nesting doll,” researcher Marc-Etienne Leveille shared in a paper detailing their findings. “We got interested in this threat because the way the Perl scripts used by the cybercriminals are packed inside ELF executables is uncommon and more complex than the average server threat.
During the period over which we collected data, we saw Mumblehard queries from 8,867 unique IP addresses. The majority of them are servers that are used for hosting websites,” says Leveille. “We can see that the number of infected hosts is slowly decreasing, but has timely increases from time to time. The operators are initiating discrete waves of server infection rather than spreading in a continuous fashion.
After analyzing the malware, they were led to Yellsoft. A company which sells a software called DirectMailer, a program for sending bulk email messages.
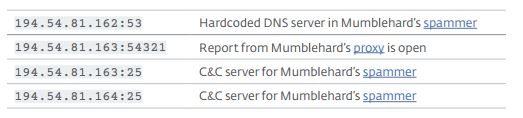
If you check out the two next IP addresses, 194.54.81.165and 194.54.81.166, you will find that both are name servers for yellsoft.net. Also, the yellsoft.netweb server is hosted at 194.54.81.166. If you dig further, the five IP addresses, from 162 to 166, will answer the same NS and SOA record for this IP range, despite the fact that in reality, this range is served by rx-name.com. This strongly suggests that the five IP addresses are hosted on the same server
Strangely enough on their homepage, it tells its visitors that they don’t offer support for cracked versions, but what is strange is that, they link the cracked version. Now, why would a company link a cracked version. It’s normal to alert its users they will not offer support but why link the crack version?
The zip archive contains a dm.pl executable file. Despite the .plextension, it is not a Perl script, but an ELF executable. This executable file contains a Perl script packed with the Mumblehard packer. Analysis of the Perl script shows that a function called bdrp is invoked before the main program is started. This function has a uuencoded blob, which, once decoded, generates another ELF file. This ELF file is a packedPerl script consisting of the Mumblehard backdoor. It is written to the file
system and a cron job is added to run it every 15 minutes.
The fact that the authors used a custom packer to hide the Perl source code is somewhat sophisticated. However, it is definitely not as complex as the Windigo Operation we documented in 2014. Nonetheless, it is worrying that the Mumblehard operators have been active for many years without disruption
Researchers are unclear of the groups goal.
It is unclear if spamming is the only goal of this group. In theory, it is possible for the cybercriminals to deploy other executable files to thousands of servers at once. Do they send other types of spam with their botnet? Is a pharmaceutical online store lucrative enough to justify the effort?
Prevention
Victims should look for unsolicited cronjob entries for all the users on their servers. This is the mechanism used by the Mumblehard backdoor to activate the backdoor every 15 minutes. The backdoor is usually installed in /tmp or /var/tmp. Mounting the tmp directory with the noexec option prevents the backdoor from starting in the first place.
You can read the white paper here.