Not one but two vulnerabilities
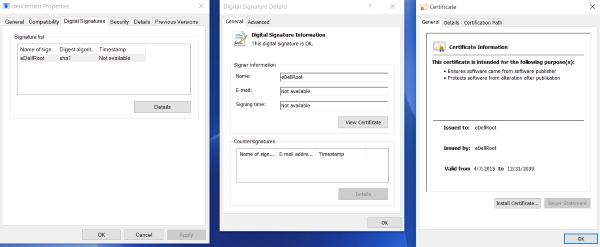
Some Dell computers are found to be vulnerable to man in the middle attack. This is because an issue with a root certificate authority. The vulnerable was discovered by Joe Nord, who pointed out that a certificate named eDellRoot which was valid till 2039. This certificate is installed by Dell, on a number of computers with private keys. The same private key is now public, this private key has been used on numerous dell computers, which opens a door for hackers.
New computer, "eDellRoot" in the list of trusted root certificates. Valid through 2039. Not a good feeling. pic.twitter.com/HqpatkwrSZ
— Joe Nord (@jhnord) November 2, 2015
Dell responded by saying that
Hackers can also sign the eDellRoot certificate, which means hackers can sign a malware disguising as a if it was from a company.
Vulnerable Dell Computers
So far only this models have been found to be vulnerable.
- Inspiron 7000 (laptop and desktop)
- Dell Orchid Touch
- Dell t4034
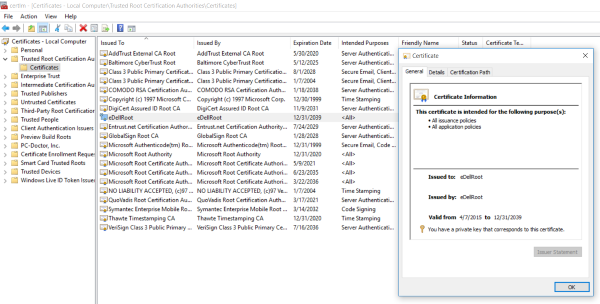
Researchers have also found another root certificate named DSDTestProvier. This certificate is similar to eDellRoot certificate. An attacker can generate certificates signed by the DSDTestProvider CA. Systems that trusts the DSDTestProvider CA will trust any certificate issued by the CA. An attacker can impersonate web sites and other services, sign software and email messages, and decrypt network traffic and other data. Common attack scenarios include impersonating a web site, performing a MiTM attack to decrypt HTTPS traffic, and installing malicious software
Mitigation
Users can revoke the DSDTestProvider certificate by launching the Windows certificate manager (“certmgr.msc”) and moving the DSDTestProvider certificate from the Trusted Root Certificate Store to Untrusted Certificates.