MAC Thunderbolt Vulnerability – Thunderstrike
As we know, if we have physical access then all bets are off. But this Vulnerability because even with clean install or replacing hard drive has no effect because the malicious code is in the system ROM , also its been more than two years and this vulnerability hasn’t been patched yet.
Share
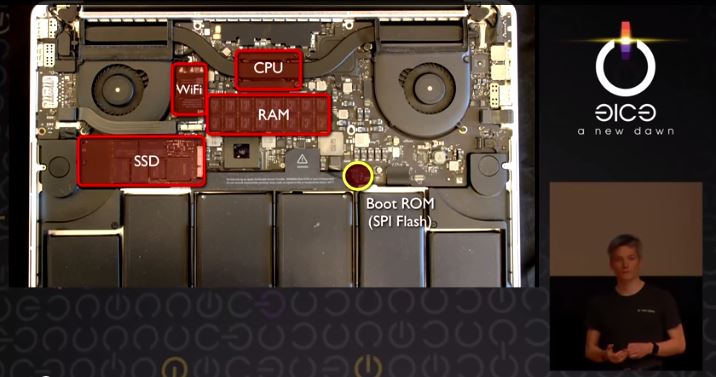
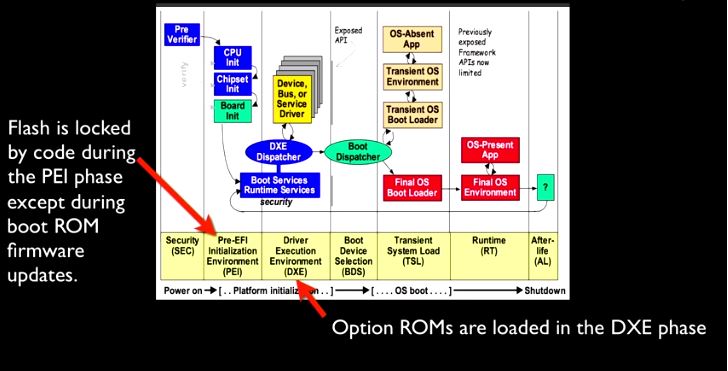
Since the boot ROM is independent of the operating system, reinstallation of OS X will not remove it. Nor does it depend on anything stored on the disk, so replacing the hard drive has no effect. A hardware in-system-programming device is the only way to restore the stock firmware.
There are neither hardware nor software cryptographic checks at boot time of firmware validity, so once the malicious code has been flashed to the ROM, it controls the system from the very first instruction,” Trammell Hudson said. “It could use SMM and other techniques to hide from attempts to detect it.
Thunderstrike: EFI bootkits for Apple MacBooks [31c3]