Service operators need to patch their servers
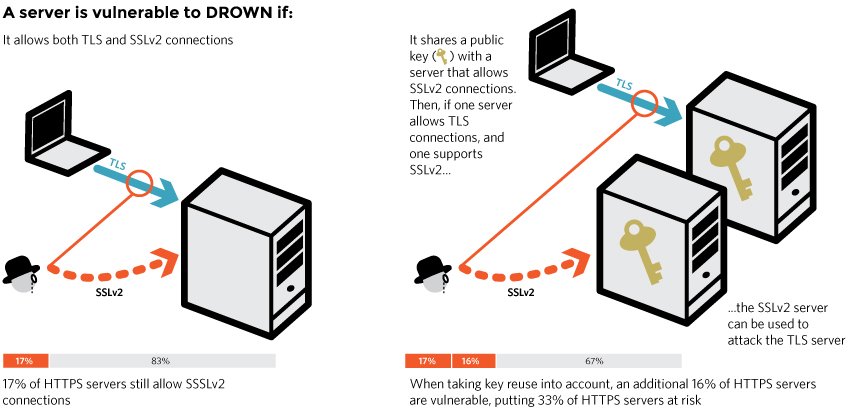
DROWN shows that merely supporting SSLv2 is a threat to modern servers and clients. It allows an attacker to decrypt modern TLS connections between up-to-date clients and servers by sending probes to a server that supports SSLv2 and uses the same private key.
Any services which rely on SSL and TLS are exposed. About 33% of internet users are affected. Attackers can steal passwords, credit card numbers, email, instant message data and more.
Due to a series of dumb mistakes on the part of a vast number of people, DROWN means that TLS connections to a depressingly huge slice of the web (and mail servers, VPNs etc.) are essentially open to attack by fairly modest adversaries – Matt Green
Matt Green continues saying this is a classic example of cross protocol attack. “This type of attack makes use of bugs in one protocol implementation (SSLv2) to attack the security of connections made under a different protocol entirely — in this case, TLS. More concretely, DROWN is based on the critical observation that while SSLv2 and TLS both support RSA encryption, TLS properly defends against certain well-known attacks on this encryption — while SSLv2’s export suites emphatically do not.”
“This is a vulnerability that has been known for a long time in the older versions of the SSL protocol, but that combined with the backdoor vulnerability caused by export crippled cryptography,” said Steve Marquess of OpenSSL. He said even though today the US government isn’t requiring those export restrictions, a lot of that export cripple cryptography code still has support, he said. The combination of the two (SSLv2 and export crippled cryptography) have created a devastating way of breaking every known implementation of SSL V2. “People shouldn’t be using either one of those implementations, but a huge numbers of websites still are,” – Marques
To protect against DROWN, server operators need to ensure that their private keys are not used anywhere with server software that allows SSLv2 connections. This includes web servers, SMTP servers, IMAP and POP servers, and any other software that supports SSL/TLS. There is nothing practical that web browsers or other client software can do to prevent DROWN. Only server operators are able to take action to protect against the attack.DROWN vulnerability can be checked here.