Not Just A Financial Threat
Not just a financial threat says the researchers at Fireye. Nemesis is a malware suite that for capturing screens, key loggers, transferring files and injecting processors. Reports stated the Trojan had been sold for $40,000 due to the addition of bootkit functionality.
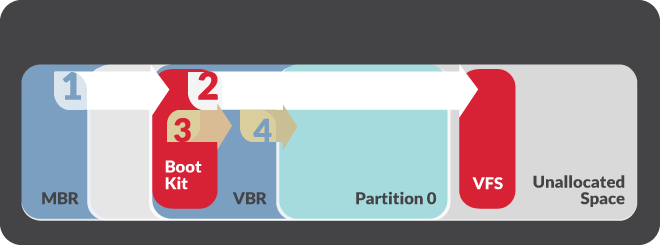
Bootkits, such as BOOTRASH, are very difficult to detect because they have the potential to be installed and executed almost completely outside of the Windows operating system. Because the malicious boot loader executes before Windows itself is fully loaded, it is not subject to typical operating system integrity checks. The components used to load the malware payload are not scanned by anti-virus software, because they are stored in a VFS outside the Windows file system.
“The threat group deployed numerous malicious files and utilities, all of which were part of a malware ecosystem referred to as ‘Nemesis’ by the malware developer(s), and used this malware to access the victim environment and steal cardholder data. FIN1, which may be located in Russia or a Russian-speaking country based on language settings in many of their custom tools, is known for stealing data that is easily monetized from financial services organizations such as banks, credit unions, ATM operations, and financial transaction processing and financial business services companies.”
The use of malware that persists outside of the operating system requires a different approach to detection and eradication. Malware with bootkit functionality can be installed and executed almost completely independent of the Windows operating system. As a result, incident responders will need tools that can access and search raw disks at scale for evidence of bootkits. Similarly, re-installing the operating system after a compromise is no longer sufficient. System administrators should perform a complete physical wipe of any systems compromised with a bootkit and then reload the operating system.
BOOTRASH has built in option for restoring original boot sector and does not remove custom virtual file system. System administrators need to make sure to do a physical wipe. Simply re installing the operating system will not remove the malware.