Really Destructive Malware, with Layers Of Obfuscation
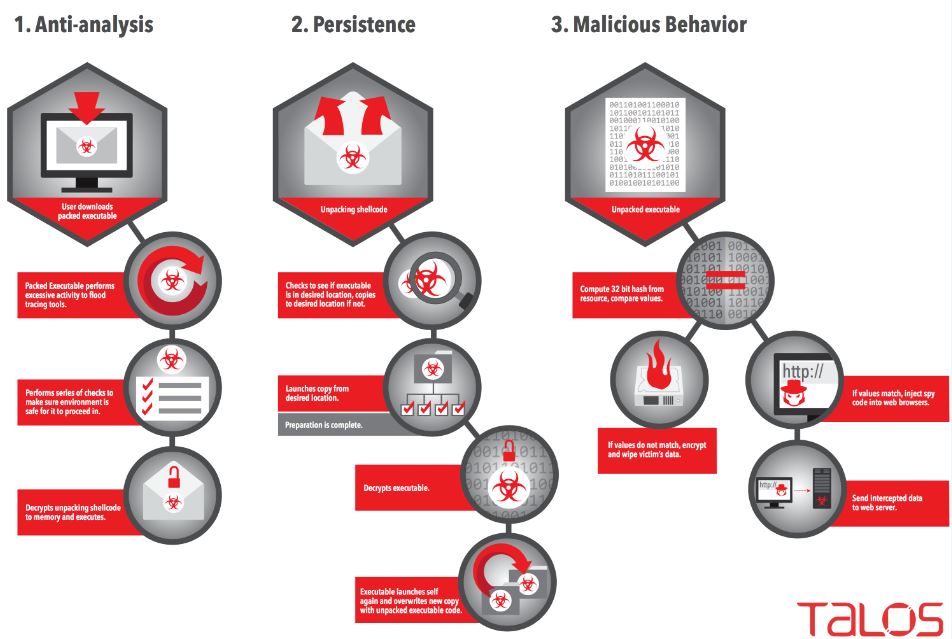
At a high level, Romberik is a complex piece of malware that is designed to hook into the user’s browser to read credentials and other sensitive information for exfiltration to an attacker controlled server. Rombertik collects information from all websites in an indiscriminate manner. It is installed onto the computers when someone downloads and unzips attachments, the email itself shows “From: Windows America”. The malware seems very complex, unlike other malware you might get through emails, this malware first checks if it is running within a sandbox. Once anti-analysis are completed, it will decry pt itself and install it on the victims machine.
After installation, it will then launch a second copy of itself and overwrite the second copy with the malware’s core functionality. Before Rombertik begins the process of spying on users, Rombertik will perform once last check to ensure it is not being analyzed in memory. If this check fails, Rombertik will attempt to destroy the Master Boot Record and restart the computer to render it unusable
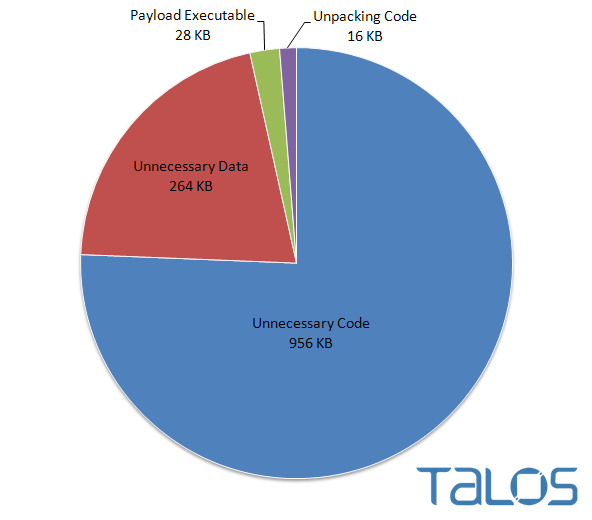
Rombertik incorporates several layers of obfuscation along with anti-analysis functionality. Obfuscating the functionality of a malware sample can be accomplished in many different ways. A common method is to include garbage code to inflate the volume of code an analyst might have to review and analyze. In this case, the unpacked Rombertik sample is 28KB while the packed version is 1264KB. Over 97% of the packed file is dedicated to making the file look legitimate by including 75 images and over 8000 functions that are never used. This packer attempts to overwhelm analysts by making it impossible to look at every function.
Once the packer has run through initial anti-analysis checks, it will check to see if it is executing from %AppData%\rsr\yfoye.exe. If the packer is not executing from there, it will proceed to install itself in order to ensure persistence across system reboots before continuing on to execute the payload. To install itself, Rombertik first creates a VBS script named “fgf.vbs”, which is used to kick off Rombertik every time the user logs in, and places the script into the user’s Startup folder. Rombertik then creates %AppData%\rsr\yfoye.bat and moves the packed version of itself into %AppData%\rsr\yfoye.exe
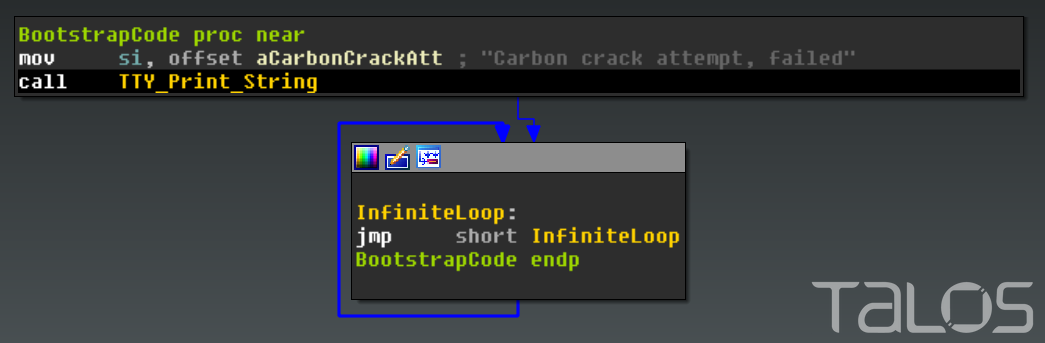
Once the unpacked version of Rombertik within the second copy of yfoye.exe begins executing, one last anti-analysis function is run — which turns out to be particularly nasty if the check fails. The function computes a 32-bit hash of a resource in memory, and compares it to the PE Compile Timestamp of the unpacked sample. If the resource or compile time has been altered, the malware acts destructively. It first attempts to overwrite the Master Boot Record (MBR) of PhysicalDisk0, which renders the computer inoperable. If the malware does not have permissions to overwrite the MBR, it will instead destroy all files in the user’s home folder (e.g. C:\Documents and Settings\Administrator\) by encrypting each file with a randomly generated RC4 key. After the MBR is overwritten, or the home folder has been encrypted, the computer is restarted.
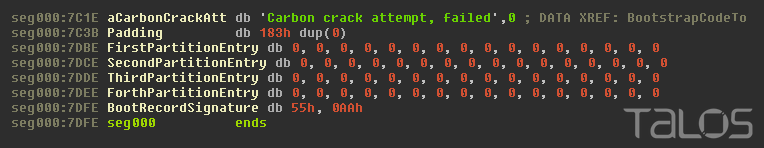
The Master Boot Record starts with code that is executed before the Operating System. The overwritten MBR contains code to print out “Carbon crack attempt, failed”, then enters an infinite loop preventing the system from continuing to boot.
If an analysis tool attempted to log all of the 960 million write instructions, the log would grow to over 100 gigabytes…Even if the analysis environment was capable of handling a log that large, it would take over 25 minutes just to write that much data to a typical hard drive, researchers explain.
As always have up to date anti virus and don’t click on emails from unknown address, but what can you really do? If you sandbox it, you will have to re-install Operating System. Best protection is just avoid unknown emails.