All For Information Security
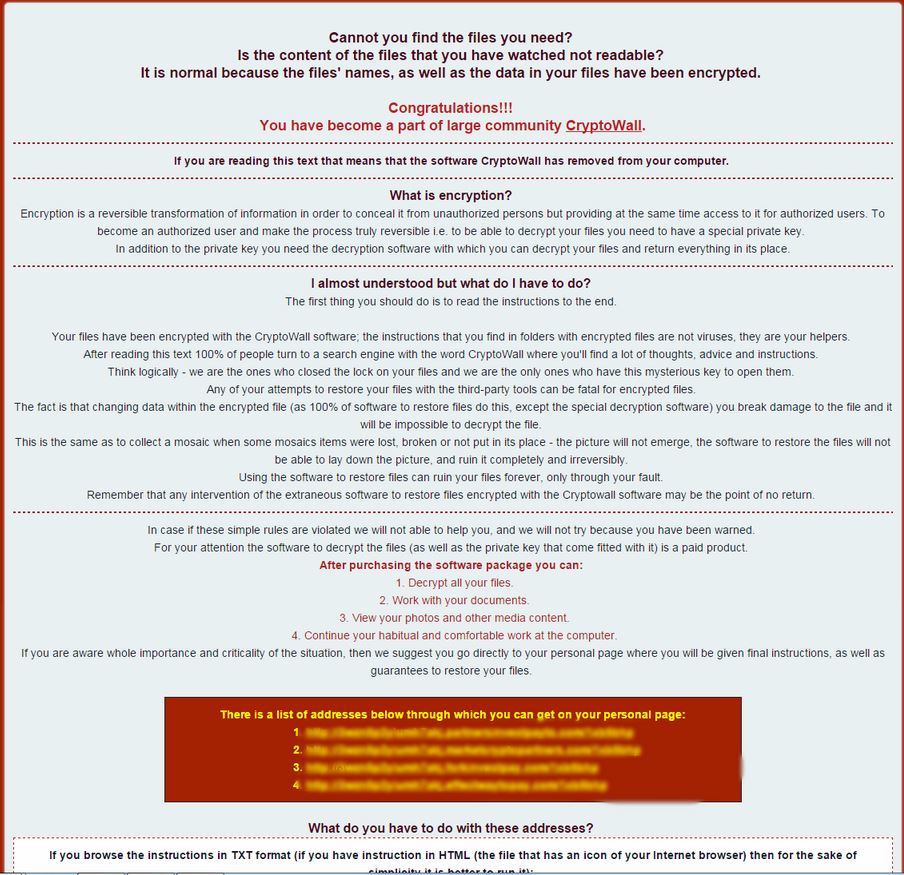
CryptoWall 4.0 still includes advanced malware dropper mechanisms to avoid antivirus detection, but this new version possesses vastly improved communication capabilities. It includes a modified protocol that enables it to avoid being detected, even by 2nd generation enterprise firewall solutions. This lowers detection rates significantly compared to the already successful CryptoWall 3.0 attacks.
Well if it just is for research purpose then why ask users 1.8 BTC, which is worth around $700. Federal reports have stated that since April 2014, Cryptowall has caused $1 Million in loses, every month. A total of $325 Million in US alone.
CryptoWall 4.0 spam servers are located in Russia. The Javascript malware is downloaded from the Russian servers. According to investigation, reveals that that AES 256 encryption is being used. Targeted countries we have identified so far include: France, Italy, Germany, India, Romania, Spain, US, China, Kenya, South Africa, Kuwait and the Philippines. Russian users seem to be safe. Also if you have Russian keyboard you are safe? May be. The malware doesn’t encrypt the files when it detects the keyboard is in Russian language.
“Cryptowall 4.0 still includes advanced malware dropper mechanisms to avoid antivirus detection, but this new version possesses vastly improved communication capabilities,”
“It includes a modified protocol that enables it to avoid being detected, even by second generation enterprise firewall solutions.”
“This lowers detection rates significantly compared to the already successful Cryptowall 3.0 attacks”.
BitDefender have created a vaccine, which protect your files from CryptoWall but it does not protect you if you have already been infected.
If you are infected you have two options at the moment. Either format your computer or pay for the ransomware. Please note that paying for ransomware does not guarantee that you will get the decryption key. Also you should never encourage cyber criminals by paying ransomware.