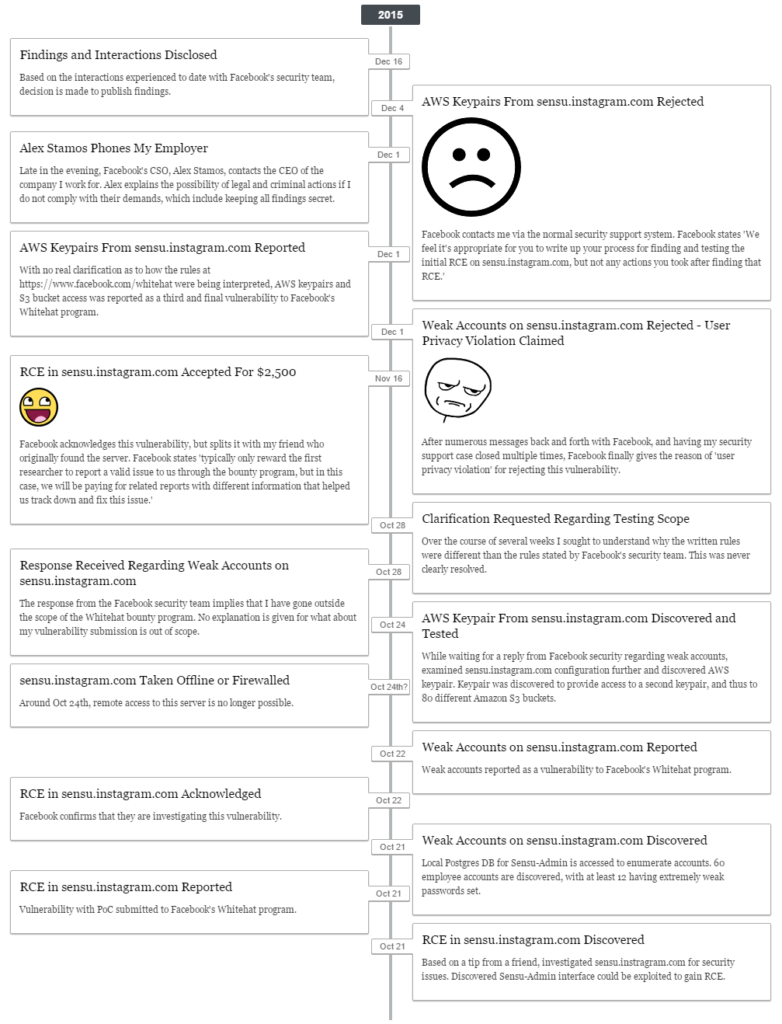
Security Researcher Violates Facebook Bounty
Security researcher, Wesley Wineberg was able to gain access to Instagram system which allowed him to access Source code, private keys and SSL certificates for Instagram.com. Essentially all findings started from an RCE on the server sensu.instagram.com. This RCE was possible due to the reuse of a Ruby secret key, and the fact that the version of Ruby allows for code execution through object deserialization. From this RCE, it was observed that the server also was configured with several users who had extremely weak passwords.
The researcher submitted the vulnerabilities in three reports, and was paid for report 1 only. Facebook warned that by accessing confidential data the bounty was invalid.
The following is the types of data that was available all using one AWS keypair, although the data was spread across multiple buckets:
- Static content for Instagram.com websites. Write access was not tested, but seemed likely.
- Source code for fairly recent versions of the Instagram server backend, covering all API endpoints, some image processing libraries, etc.
- SSL certificates and private keys, including both instagram.com and *.instagram.com
- Secret keys used to sign authentication cookies for Instagram
- OAuth and other Instagram API keys
- Email server credentials
- iOS and Android app signing keys
- iOS Push Notifications keys
- Twitter API keys
- Facebook API keys
- Flickr API keys
- Tumblr API keys
- Foursquare API keys
- Recaptcha key-pair
The Vulnerability submission for this third finding included 7 different issues, These were:
- AWS credentials accessible to unprivileged user on Sensu system.
- AWS bucket contain credentials for other buckets (specifically autoscale-kitchen). This is a classic privilege escalation weakness
- No access segregation on AWS credentials. Using one set of AWS keys I was able to access all S3 buckets.
- “Secret keys” stored throughout S3 buckets. This is furthered by the fact that some buckets no longer contain keys in their latest application version, but the bucket contains all previous application versions. These keys do not appear to be separated properly so that one application can only access keys appropriate to its application, but they are spread out across multiple buckets
- Files stored in some buckets are encrypted to passwords also stored in the same bucket (or accessible via the same AWS key)
- AWS keys can be used from any remote IP.
- If audit logging takes place, it is not monitored in any way as none of my access was detected (as far as I am aware).
“If you give us reasonable time to respond to your report before making any information public, and make a good faith effort to avoid privacy violations, destruction of data, and interruption or degradation of our service during your research, we will not bring any lawsuit against you or ask law enforcement to investigate you.” said Facebook
“In my opinion, the best course of action was to simply be transparent with all of my findings and interactions. I am not looking to shame any individuals or companies, but I do believe that my treatment in this situation was completely inappropriate” – Wesley Wineberg