New SMB Vulnerability allows hackers to steal login credentials
The flaw released by Cyclance, shows how an attacker can get login credentials of a user if the attacker has access to the network. While the credentials are encrypted, the encryption method used were devised in 1998 and for today’s technology it is weak. This research is a extension to a previous research which was carried out 18 years ago.
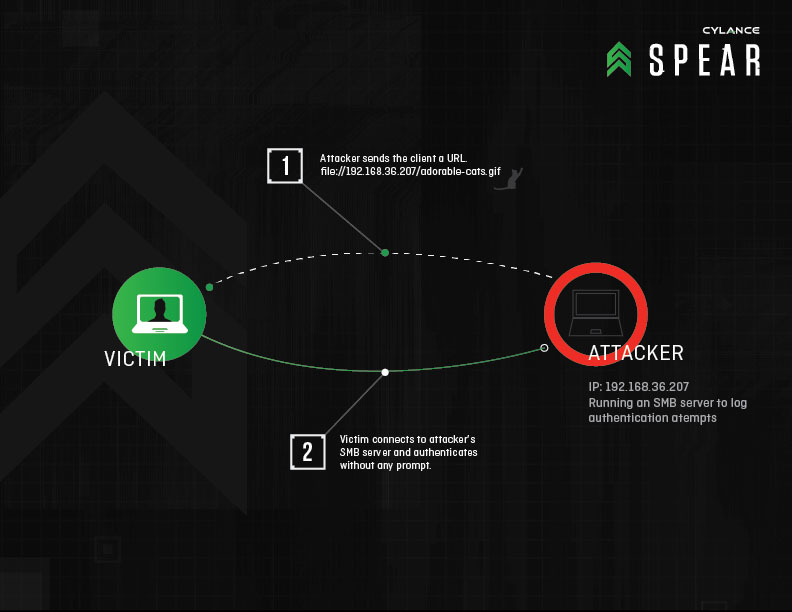
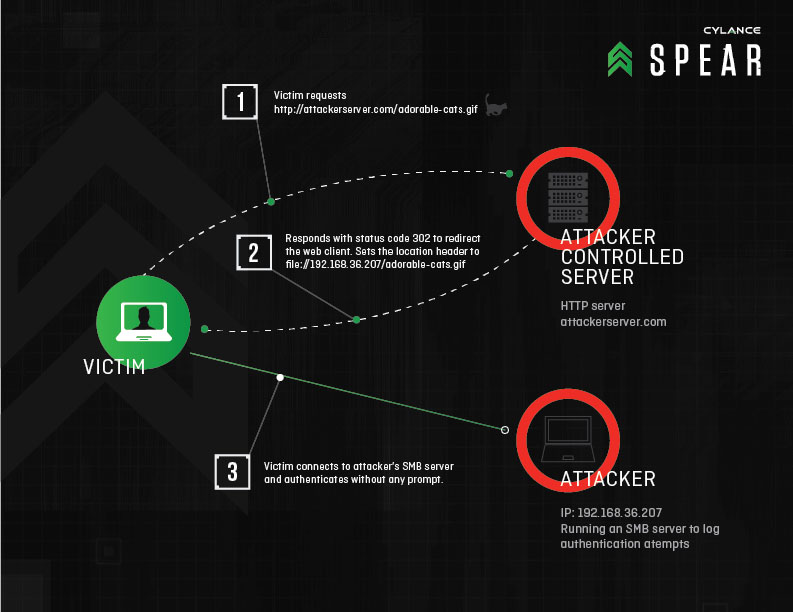
Redirect to SMB is a way for attackers to steal valuable user credentials by hijacking communications with legitimate web servers via man-in-the-middle attacks, then sending them to malicious SMB (server message block) servers that force them to spit out the victim’s username, domain and hashed password
The Redirect to SMB attack builds on a vulnerability discovered in 1997 by Aaron Spangler, who found that supplying URLs beginning with the word “file” (such as file://1.1.1.1/) to Internet Explorer would cause the operating system to attempt to authenticate with a SMB server at the IP address1.1.1.1. It’s a serious issue because stolen credentials can be used to break into private accounts, steal data, take control of PCs and establish a beachhead for moving deeper into a targeted network. These “file” URLs could be provided as an image, iframe, or any other web resource resolved by the browser.
We uncovered Redirect to SMB while hunting for ways to abuse a chat client feature that provides image previews. When a URL to an image was received, the client attempted to show a preview of the image. Inspired by Aaron’s research some 18 years ago, we promptly sent another user a URL starting with file:// which pointed to a malicious SMB server. Surely enough, the chat client tried to load the image, and the Windows user at the other end attempted to authenticate with our SMB server
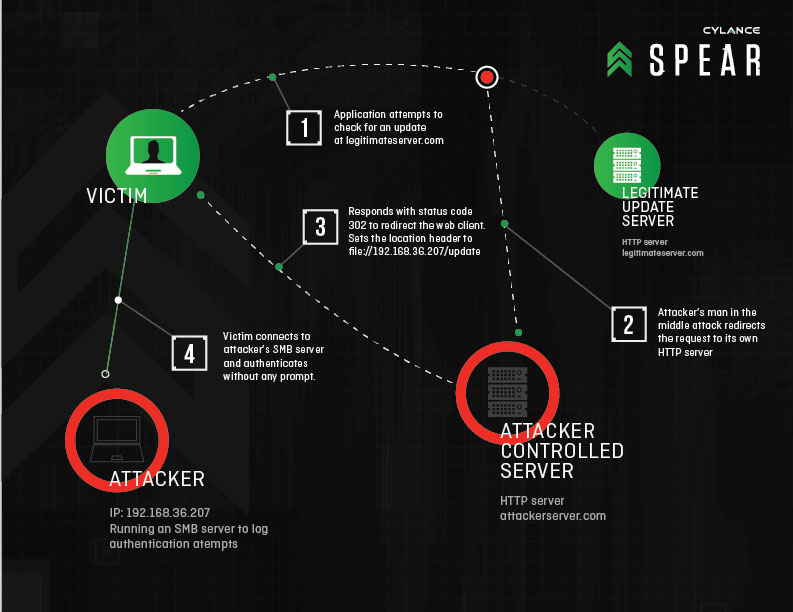
On a Windows 8.1 laptop, at least 50 different HTTP connections were made after a restart and within 5 minutes, most of which could be hijacked by a network-local attacker to force SMB authentication to a malicious service. The source of these connections ranged from OEM “update” checks to weather and news applications.
Senior Researcher at Kaspersky Lab had this to say:
I would expect this vulnerability to be used as part of a two-stage phishing attack: First try to exploit vulnerabilities, including this one, after getting the user to click a link in an email, and then attempt to do something further by getting the user to “log in” to a fake portal, or downloading software that takes over the machine. In this way, attackers can be moderately effective even if the user doesn’t fall for anything after opening the page
Affected applications so far. Dozens of applications were tested and 31 vulnerable applications were found.
Widely Used Applications:
Adobe Reader, Apple QuickTime and Apple Software Update (which handles the updating for iTunes)
Microsoft Applications:
Internet Explorer, Windows Media Player, Excel 2010, and even in Microsoft Baseline Security Analyzer
Antivirus:
Symantec’s Norton Security Scan, AVG Free, BitDefender Free, Comodo Antivirus
Security Tools:
.NET Reflector, Maltego CE
Team Tools:
Box Sync, TeamViewer
Developer Tools:
Github for Windows, PyCharm, IntelliJ IDEA, PHP Storm, JDK 8u31’s installer
So how can i fix it? What can i do?
Well at the moment, Microsoft have not released a patch for this vulnerability. Also the research which was done 18 years, at that time Microsoft did not resolve this vulnerability, wonder how many credentials have been stolen.
The simplest workaround is to block outbound traffic from TCP 139 and TCP 445 — either at the endpoint firewall or at the network gateway’s firewall (assuming you are on a trusted network). The former will block all SMB communication, which may disable other features that depend on SMB. If the block is done at the network gateway’s firewall, SMB features will still work inside the network, but prevent authentication attempts with destinations outside the network